they don t know about us แปล: คุณกำลังดูกระทู้
 Yes, the truth is out there. But they don’t want you to know about it.
Yes, the truth is out there. But they don’t want you to know about it.
Who’s “they”? It could be Google or product manufacturers, your boss or your wireless carrier, Hollywood or Uncle Sam.
What don’t they want you to know? That your cell phone, your Webcam, and your employer may be spying on you. That you’re probably paying too much for printer ink, and that your wicked-cool subsidized handset will cost you way more over time than an unsubsidized one. That your PC may be coated with toxic flame retardants. And that’s just for starters.
Don’t despair. For every dirty little secret revealed herein, we describe a fix or a way to work around it (if any exists). You don’t have to be a victim, if you know what to do.
Just remember: You’ve been warned.
Table of Contents
Your ISP Is a Copyright Cop
The RIAA and the MPAA may have a new ally. The next people who bust you for illegally swapping music and movies could be the folks you pay for Internet access.
 The recording and film industries are seeking to manipulate upcoming net neutrality legislation to allow ISPs to scan the bits passing through their networks and to block any that may violate copyrights–similar to Comcast’s notorious attempts to throttle BitTorrent connections in 2007. The Federal Communications Commission’s recommended rule changes already contain an exception for “reasonable network management,” which could include sniffing for copyrighted content, says Jennifer Granick, civil liberties director for the Electronic Frontier Foundation.
The recording and film industries are seeking to manipulate upcoming net neutrality legislation to allow ISPs to scan the bits passing through their networks and to block any that may violate copyrights–similar to Comcast’s notorious attempts to throttle BitTorrent connections in 2007. The Federal Communications Commission’s recommended rule changes already contain an exception for “reasonable network management,” which could include sniffing for copyrighted content, says Jennifer Granick, civil liberties director for the Electronic Frontier Foundation.
Meanwhile, according to leaked reports, the international Anti-Counterfeiting Trade Agreement (ACTA) now being negotiated in private sessions contains provisions requiring ISPs to police their own networks for copyright scofflaws. Critics of the proposed treaty fear that copyright holders will insert a “three-strikes” policy, under which users could have their Internet access revoked if they’re caught exchanging copyrighted content more than twice.
“It’s dangerous giving so much power to copyright claims,” says Wendy Seltzer, project leader for the Chilling Effects Clearinghouse and a Fellow at Harvard’s Berkman Center for Internet & Society. “Imagine someone telling you, ‘If you violate our copyrights, we can terminate your Net connection, not just your blog.’”
With such a powerful new partner playing the role of both investigator and enforcer, might copyright holders be emboldened to pursue more consumers suspected of violating copyrights? And what protections will consumers have against false claims of infringement?
The Fix: Contact your congressional representatives and tell them that you oppose net neutrality loopholes for content filtering. Support organizations such as Chilling Effects, the EFF, and Public Knowledge, which fight laws that turn ISPs into Hollywood’s hired guns.
Cell Phones Don’t Crash Airplanes
The Federal Communications Commission and the Federal Aviation Administration have each recommended that airlines not allow passengers to use cell phones during commercial flights. The FAA fears that the RF signal emitted by devices using the 800MHz spectrum band might interfere with the navigation systems of the plane, specifically GPS instrumentation. Yet there is no documented case of an air accident or serious malfunction caused by a cell phone’s interfering with a plane’s navigation system.
The FCC’s concern is that wireless networks on the ground might be disrupted by the cell phones flying overhead. As a plane flies over a wireless cell tower on the ground, the FCC believes, the cell site will detect all the cell phones operating inside the plane and go to work registering those devices to operate on the network. But by the time the tower registers and connects all those mobile phones passing overhead, the plane will have passed into the range of the next cell tower on its route. This uses up system resources and could hurt network performance for connected phones on the ground.
But some experts believe that this worry is outdated. “Color me highly skeptical that this is a real problem with modern systems,” says Ken Biba, CTO of Novarum, a wireless consulting and engineering group. “Modern digital phones actually use lower power, and, further, the cell towers have very directional antennas designed for covering the surface of the earth [not the air above].”
The Fix: There isn’t much you can do. Actually, the FCC and the FAA are doing us a big favor here. They’re delivering us from having to fly with people jabbering away on their cell phones from takeoff to landing.
‘Private’ or ‘Incognito’ Browsing…Isn’t
These days, most major Web browsers offer “private” or “incognito” browsing (known colloquially as “porn mode”). But all the feature really does is tell your browser not to record the sites you’ve looked at, the search terms you’ve used, or the cookies deposited during that session.
If the sites you visit record your IP address (and many do), that information is available to any interested party that has the legal right to request it–a group that can include divorce attorneys and law enforcement. Recording visitors’ IP addresses is a trivial task–you can add to any blog a free widget that accomplishes the same thing–so you should assume that the sites you visit do so.
Of course, your Internet service provider assigned you the IP address in the first place, so it can track you anywhere you go online, if it so chooses. In fact, the FBI wants ISPs to store your surfing histories for at least two years. So far, major ISPs have resisted this push, in part because the storage and record-keeping requirements would be enormous. What information ISPs retain, how long they keep it, and how public they are about it vary from provider to provider–most won’t talk about it. (One exception is Cox Communications, which says that it retains IP address logs for six months.) So while your spouse may not know what you’ve been up to online, the feds might.
The Fix: If you really want to browse off the record, use a proxy service, like Anonymizer or Tor, that obscures your IP address as you surf.
You’re Spending Too Much on Printer Ink
If there was ever a business built around scare tactics, it’s the business of selling inkjet printers. Try using a refurbished or refilled cartridge, and the printer maker may warn you that you’re voiding your service warranty, putting your printer at risk of damage, or possibly ruining your printouts.
 Nonsense, says Bill McKenney, CEO of InkTec Zone, which sells equipment for refilling inkjet cartridges to retailers such as Wal-Mart International.
Nonsense, says Bill McKenney, CEO of InkTec Zone, which sells equipment for refilling inkjet cartridges to retailers such as Wal-Mart International.
“You won’t void the warranty and you won’t hurt your printer,” says McKenney. “A bad refill job may leak ink inside your machine. Otherwise you’ll be fine. And the savings are so significant, there’s almost no reason not to do it.”
In fact, PCWorld’s own lab testing shows that while prints made with third-party, refurbished, or refilled ink cartridges aren’t always as good as those made with the printer manufacturer’s ink, the cartridges are safe to use in your printer.
The exceptions are so-called prebate cartridges, sold at a slight discount, that contain a chip preventing their being refilled (which should be clearly labeled as one-use-only products).
The Fix: Buying a refurbished cartridge can save you 10 to 20 percent off the price of a new one. Getting refills bumps that savings to 50 percent or more.
The drawbacks are that you may not get quite as much ink with a refill (the amount is usually at least 95 percent, McKenney says), archival prints may not maintain their color quality for as long, and you can refill each cartridge only three to eight times before you’ll have to recycle it and get a new one.
End User License Agreements May Not Be Enforceable
It doesn’t take much effort to sign an end user license agreement: Rip open a software package, or tick a box on a Website, and you’re legally bound. But your obligations depend a lot on where you live, says Jonathan Ezor, director of the Institute for Business, Law & Technology at the Touro Law Center on Long Island.
“EULAs are contracts, and contract law is state law,” says Ezor. “It’s governed by the state where you live or where the company is based.” For example, courts in the Third Circuit Court of Appeals (Delaware, New Jersey, and Pennsylvania) and the Fifth Circuit Court of Appeals (Louisiana, Mississippi, Texas) have found certain types of EULAs invalid.
Other factors include whether the agreement contains unenforceable restrictions, whether it gives consumers sufficient choice, and what method it provides for users to indicate agreement, Ezor adds.
The odds of your going to court over a EULA, however, are slight. The real issue is how companies enforce them, Ezor says.
“What companies really don’t want you to know is how easy it is for them to turn things off or erase them,” he adds. “Think of what happened last year with the Orwell books that Amazon just erased from people’s Kindles.”
The Fix: Read the EULA. Does the software “phone home” to verify that you’re using the product as its creator intended–and, if you’re not, does it have the ability to disable the program remotely? If it doesn’t, you’re probably free to do as your conscience allows.
The Cyberwar Is Heating Up (and Uncle Sam Is Losing)
We may be at war on the ground in Afghanistan, but bigger battles are being waged beneath the noses of most Americans. For the past several years, U.S. government computer networks have been under siege from foreign adversaries. What the people in charge don’t want you to know is that it could have been prevented.
Attacks on Department of Defense computer systems jumped 60 percent in 2009, according to a congressional committee. Last July, a botnet originating in North Korea launched a sustained DDOS attack on several U.S. government agencies, including the Federal Trade Commission and the Department of the Treasury. In December, China was fingered for attacks that compromised Google last December but also targeted top government research firms, contractors, and think tanks.
Testifying before Congress in February, former national intelligence director Mike McConnell said the United States may be on the brink of an all-out cyberwar–one we are unprepared to fight.
“From the beginning the government’s approach to networks was to facilitate access,” says Richard Stiennon, chief research analyst for IT-Harvest and author of Surviving Cyber War. “Now that seems naïve. E-mail is its primary means of communications, and that’s completely exposed. Attackers from all over are having their way with government computer systems.”
The Fix: “Joe and Jane Citizen need to tell the federal government to comply with computer security standards published by the National Institute of Standards and Technology (NIST),” says Stiennon. “That will get us about 90 percent closer to where we need to be, so we can start focusing on the real bad guys.”
Google Could Rat You Out
How much does Google know about you? That depends on how much you rely on its cornucopia of free services. But that stored information may easily include the Websites you visit, the search terms you use, the maps you view, your contacts and calendar, your e-mail messages, your chat history, Google Voice phone records, YouTube videos and Picasa photos, the documents you store online, your blogs and advertising accounts, your status updates on Google Buzz, your location on Google Latitude, and–if you use an Android handset–all the data associated with your cell phone, too.
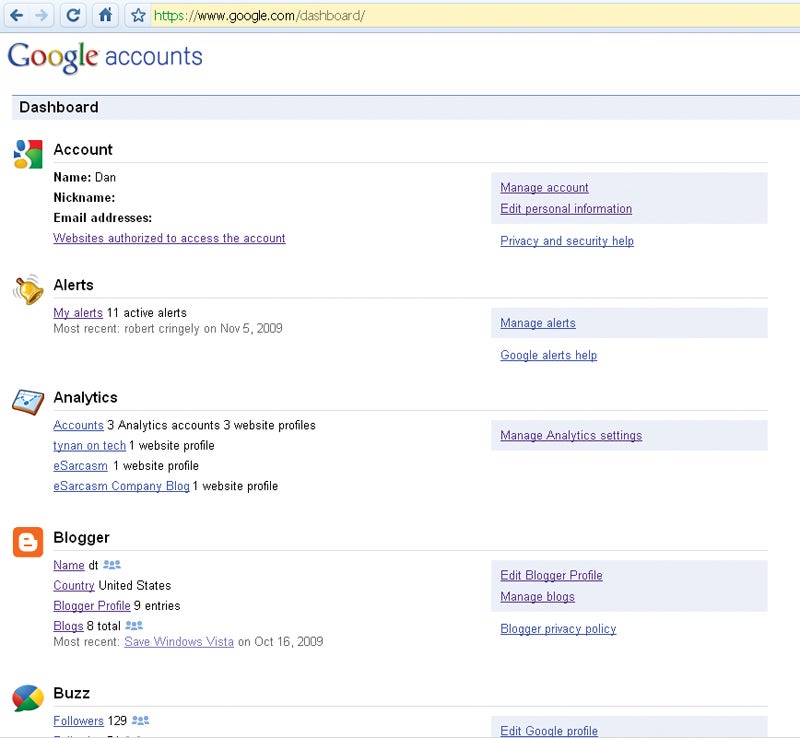 If the government comes knocking with a subpoena–or even just a strongly worded letter, per the Patriot Act–Google is obligated to hand everything over. Sure, the feds can get this data from anyone, but Google’s wealth of information (as well as its lengthy data-retention policies) makes their job much easier.
If the government comes knocking with a subpoena–or even just a strongly worded letter, per the Patriot Act–Google is obligated to hand everything over. Sure, the feds can get this data from anyone, but Google’s wealth of information (as well as its lengthy data-retention policies) makes their job much easier.
Even if you have nothing to hide from the authorities, all that stands between you and Christmas in July for an identity thief is your Gmail log-on and password; that’s the key that unlocks every other Google service. Last October, Google reported that thousands of Gmail accounts had been compromised by a phishing scheme that also targeted AOL, MSN Hotmail, and Yahoo. Even sophisticated users have had their Gmail accounts hijacked. Little wonder, then, that Chinese hackers targeted Gmail accounts when they compromised the service last December.
The Fix: Use Google Dashboard to see what information you’re sharing (prepare to be blown away), and adjust your settings accordingly. Make your Gmail password harder to guess, and change it every couple of months. If you think your Gmail account has been hacked or stolen, you may be able to use Google’s account-recovery page to get it back. And given Google’s recent stumbles over user privacy with Buzz, you might consider spreading the risk over different providers.
Pacemakers and Other Implants Can Be Hacked
Researchers at the University of Washington have demonstrated that medical implants that rely on wireless technologies for monitoring the devices and adjusting their settings are not secure.
In lab tests, scientists from UW, the University of Massachusetts Amherst, and Harvard Medical School were able to take control of a cardiac defibrillator and use it to induce ventricular fibrillation, a potentially lethal condition. They could also read sensitive medical information stored on the device and change it at will.
Study coauthor Tadayoshi Kohno, assistant professor at the University of Washington, says that similar techniques theoretically could be applied to other wireless medical devices, such as drug dispensers and neuro-stimulators.
“Medical devices are innovating at an extremely rapid pace,” says Kohno. “In the future they’ll be much more like full-grown computers. We did this study to raise awareness and increase our understanding of the security risks these devices could pose.”
The Fix: At present no fix exists, though the Food and Drug Administration and medical-device manufacturers are aware of the problem. There are no known cases of medical devices being hacked in the wild.
Even the study’s coauthor downplays the actual danger. “The risk to patients today is low,” adds Kohno. “These are amazing life-saving devices, and I would have no qualms about using one.”
Your PC May Be Killing You
Though electronics manufacturers have made great strides in reducing their use of harmful chemicals in recent years, tech gear still may contain brominated flame retardants–chemicals used to reduce the risk of fire that studies have linked to lower IQs in children and reduced fertility rates.
 “BFRs used in the manufacture of circuit boards can be converted to highly toxic brominated dioxins and furans if the products are burned at the end of their life,” says Arlene Blum, executive director of the Green Science Policy Institute and a visiting professor of chemistry at UC Berkeley.
“BFRs used in the manufacture of circuit boards can be converted to highly toxic brominated dioxins and furans if the products are burned at the end of their life,” says Arlene Blum, executive director of the Green Science Policy Institute and a visiting professor of chemistry at UC Berkeley.
But even daily use can be dangerous, says Blum. “When used in plastic casings, BFRs can also migrate out of the plastic into the dust in the room and then enter the body via the hand-to-mouth contact.”
The Fix: While major manufacturers such as Apple, Dell, and HP have moved away from BFRs in recent years, certain products built before 2009–especially devices that generate a lot of heat, like laptops and laser printers–may still contain BFRs, says Michael Kirschner, associate director of the Green Science Policy Institute. “Do some research,” says Kirschner. “Almost all vendors now have an environmental section on their Websites that tells you about the materials they use.”
The news isn’t all bad, he adds. “Most manufacturers in the consumer arena have gotten the message to get additive BFRs out of their products.”
As for older products still in people’s homes? “They probably need to be replaced anyway, right?” Kirschner jokes.
Antivirus Software Won’t Protect You
 Security programs won’t really protect you from the Internet’s worst nasties. “Antivirus software only catches the low-hanging fruit,” says Mark Kadritch, CEO of The Security Consortium and author of Endpoint Security. The increasing number of zero-day vulnerabilities–coupled with some vendors’ failure to fix security holes in their products for months or even years–means that even the most up-to-date antimalware products may still be behind the curve when it counts, he says.
Security programs won’t really protect you from the Internet’s worst nasties. “Antivirus software only catches the low-hanging fruit,” says Mark Kadritch, CEO of The Security Consortium and author of Endpoint Security. The increasing number of zero-day vulnerabilities–coupled with some vendors’ failure to fix security holes in their products for months or even years–means that even the most up-to-date antimalware products may still be behind the curve when it counts, he says.
The Fix: You can’t do without security software (see our Security Info Center for reviews of the latest security packages, plus how-tos and news), but to protect yourself more effectively you need to take extra steps such as saving your data to encrypted drives and installing VMware or other software that lets you create virtual machines and discard them as they become infected.
“At the end of the day, if you suspect your system has been compromised, blow it away and click ‘restore’ in VMware,” Kadritch says. “You may lose some e-mail, but you’ll get a brand-new system with the latest, greatest updates.”
Your Cell Phone Is a Homing Beacon
We’ll bet that you never leave home without your handset. Well, guess what: Wherever you roam, you can be found. You don’t even need a GPS chip in your phone–your using cell towers allows your provider to triangulate your position within a few hundred yards.
 “Wherever you carry your phone, the government can go to your wireless provider and use those records to figure out where you are,” says the Electronic Frontier Foundation’s Jennifer Granick.
“Wherever you carry your phone, the government can go to your wireless provider and use those records to figure out where you are,” says the Electronic Frontier Foundation’s Jennifer Granick.
Of course, this information could save your life; cell phone tracking has assisted in locating kidnap victims and people stranded in the wilderness. But law enforcement has also used the technology to track people without probable cause. Documents obtained via a Freedom of Information Act lawsuit by the ACLU, the EFF, and the Center for Democracy and Technology reveal that the state of New Jersey obtained cell phone subscriber information 79 times between 2002 and 2008 without seeking a warrant.
Giving law enforcement free rein opens up broad opportunities for information gathering on people who aren’t even necessarily persons of interest in an investigation, says Granick.
“One example would be that police could find out the names of everyone who was near a political protest site just because they were investigating someone or something that happened there,” she says.
At press time, a federal appeals court was set to hear arguments in the New Jersey case. How the court rules may determine how much of a snoop your phone continues to be.
The Fix: If your handset has a GPS chip and you don’t want to be tracked, turn it off. Even then, the carrier may be able to ping your phone to determine the cell towers nearest you. Turning off your phone entirely is your best bet for dropping off the grid, if only temporarily. The next time you use your handset, though, you’ll be back on your carrier’s grid.
A ‘Cheap’ Smartphone Is a Rip-Off
Your wireless company might like you to think that your handset is locked to one carrier for myriad technical reasons, but there’s really only one reason: profits. The carrier wants to lock you into paying hundreds of dollars a month for mobile voice and data service, and to accomplish that it will sell you a subsidized smartphone for much less than the company paid for it.
Spending more up front for an unsubsidized phone, however, might save you money in the long run. PCWorld contributing editor JR Raphael compared the fees for an unsubsidized $529 Nexus One phone (and an à la carte contract with T-Mobile) with those for the iPhone 3GS and the Motorola Droid, which are available only with a two-year contract (from AT&T and Verizon, respectively). The cost savings over two years: $1350, thanks largely to T-Mobile’s $80-per-month unlimited voice, text, and data plan (no contract required).
It gets better. Ben Ferguson, on his Nosugrefneb blog, compared a subsidized $295 Nexus One plus a two-year T-Mobile plan with an unsubsidized model using a $40 T-Mobile data plan and a $3-per-month VoIP account on Skype. Using the data plan and VoIP lopped an additional $482 off the cost–making that option $1800 cheaper than a subsidized iPhone.
The Fix: Do the math. As more vendors move toward an “open” handset model, paying more up front can save you a bundle in the long run.
Your Webcam May Be Watching You
 Two-way video chat is fun. One-way chat–where you’re the one being watched–is not so much fun. But it’s more common than you might think.
Two-way video chat is fun. One-way chat–where you’re the one being watched–is not so much fun. But it’s more common than you might think.
In February, school officials in southeastern Pennsylvania found themselves in hot water after they installed software on school laptops that allowed them to activate students’ Webcams remotely. The school claimed that the software–which could snap a picture of whoever was using the MacBook at any time–was only for locating lost or stolen laptops. Outraged parents sued the district, and the story made international headlines.
Two weeks earlier, a woman reported being spied on via her Webcam by a Dell support technician, which she discovered when she realized the tech had turned on her Webcam without asking permission. Chinese cyberspy network GhostNet has reportedly taken over at least 1300 PCs worldwide, including the ability to operate their Webcams. In 2006, Spanish authorities arrested two teens after they hacked Webcams at a local college and tried to blackmail students caught in compromising situations. In 2004, an online intruder commandeered the computer of a 15-year-old girl in Houston, operating her Webcam remotely and typing messages on her screen about the clothes she was wearing.
The Fix: If you have an external Webcam, unplug it when you’re not using it. If your camera is built in, covering the lens with a sticky note should do the trick.
Your Boss Can (and Probably Does) Monitor Your Computer
Paranoia, schmaranoia. If you work in a medium-size or large organization, the folks in your IT department are keeping tabs on you.
Using software like Websense Triton or Barracuda Purewire, they can monitor the sites you visit, and scan the e-mail you send or receive. They can also check network-activity logs, or use software that captures your keystrokes or periodically grabs images off your screen.
According to the most recent surveys conducted by the American Management Association, two-thirds of all employers monitor employee Web and e-mail activity. About four out of ten use keyloggers or snoop around employees’ computer files. And one out of four firms has fired employees for Internet-related misdeeds.
Besides boosting productivity, companies are trying to avoid malware infestations, accidental leaks of confidential data, and liability for sexual-harassment suits if employees are exposed to Internet porn.
The problem? Selective enforcement, says Joe Rose, a labor-rights attorney based in Sacramento, California. Companies just collect the information and use it when needed to weed out troublemakers, complainers, or people who rub them the wrong way. “In my experience,” Rose says, “companies use this information selectively, either to pile on evidence in case of employee misconduct or if the employee engages in activity the company doesn’t like, such as labor organizing.”
The Fix: Don’t use company gear or networks to conduct personal business. If your employer gave you a BlackBerry, get your own cell phone, says Rose. Want to check your private Webmail account? Do it from your own computer and on your own network. In nearly all cases, your privacy rights at work are minimal at best.
You Can Fight the RIAA and Win
Organizations such as the Recording Industry Association of America and the Motion Picture Association of America can have your Website taken down simply by sending an e-mail to your host or Internet service provider–even if you’ve done nothing wrong. Under the endless gift to copyright holders known as the Digital Millennium Copyright Act, service providers may avoid liability by immediately removing material alleged to violate copyrights. They don’t require proof, and they don’t have to notify you in advance.
If your materials don’t infringe copyrights, however, you can file a DMCA counter-notification with your service provider. If the copyright holder doesn’t file suit against you within 14 days, your provider must restore what it deleted. (Of course, if the copyright holder calls your bet and files suit, you can withdraw your claim. Otherwise you’ll need to lawyer up, so pick your battles carefully.)
Unfortunately, service providers don’t always provide sufficient notice for site owners after the takedown; in some cases bloggers don’t even know which files to remove. Recently, six music bloggers had years’ worth of MP3 archives wiped from Blogger.com after Google received DMCA takedown notices from the International Federation of the Phonographic Industry. One site was reinstated, while a few others changed Web hosts; the rest were still dark as of this writing.
The Fix: Mail or fax your provider a counter-notification ASAP (e-mail isn’t an option). You’ll find a fill-in-the-blanks form at the Chilling Effects Clearinghouse site.
Your Passport Could Make You a Target for Crime–Wirelessly
 Most American travelers are only dimly aware of a radio frequency ID chip embedded in the last page of their U.S. passport. The only indication as to the RFID chip’s presence is a small icon on the cover. The RFID chip permits a passport control officer to transfer the information on the passport’s “data page” wirelessly to a terminal, but security researchers have expressed concern that the range from which any RFID reader can pull data from a passport is far greater.
Most American travelers are only dimly aware of a radio frequency ID chip embedded in the last page of their U.S. passport. The only indication as to the RFID chip’s presence is a small icon on the cover. The RFID chip permits a passport control officer to transfer the information on the passport’s “data page” wirelessly to a terminal, but security researchers have expressed concern that the range from which any RFID reader can pull data from a passport is far greater.
In 2006, security firm Flexilis demonstrated the ability to read RFID data at a range of several hundred feet, using a special antenna mounted to the stock of a sniper rifle (which the researchers used for both dramatic effect and ease of aiming). Last year, Chris Paget of the security firm IOActive drove around San Francisco and, within 20 minutes, copied all of the stored data right out of two unsuspecting U.S. passport holders’ pockets, using just a laptop plus off-the-shelf hardware and software costing a total of $250.
The Fix: “The privacy risks posed by RFID-enabled passports make dumpster diving for credit card slips look like child’s play,” says Andrew Brandt, lead threat research analyst for Webroot. “If a few hundred bucks’ worth of gear is all it takes to engage in mass identity theft, or to target citizens of a specific country for crime, it doesn’t seem too unreasonable to carry your travel documents wrapped up in aluminum foil.”
The Social Web Never Forgets
If you have an ugly encounter with someone in person, odds are you’ll both forget most of it within a week. Experience the same thing on the Internet, and it will be preserved forever. Worse, people have lost jobs, gotten sued, been arrested, or endured endless embarrassment due to things they said in e-mail or posted on Facebook.
“The Internet never forgets,” says the University of Washington’s Tadayoshi Kohno. “In the old days, if you wanted to make data disappear from your computer, you could take out your hard drive and take a sledgehammer to it. Today, much of our data is in the cloud. There’s no single hard drive to smash any more.”
The Fix: Kohno and other UW researchers have developed a technology called Vanish, which adds a “self-destruct” expiration mechanism to data shared across the Net. Vanish works by encrypting text and then distributing pieces of the encryption key across a dozen peer-to-peer networks. After a specified period of time, Vanish starts losing the keys, making the data unrecoverable. It can work with e-mail or with any text entered into a Web form, Kohno says. Though Vanish is still just a research project, curious users can download its open-source Firefox plug-in.
You Can Escape Almost Any Service Contract Without Penalties
You say you agreed to a two-year service contract to get a healthy discount on your broadband service or smartphone? You may be able to ditch your obligation without having to pay the usual early-termination fee–if your service provider has changed the terms on you in the time since you signed up.
Last December, Sprint sent a notice to its customers alerting them to a 40-cent monthly increase on all lines and a $5 increase on accounts with spending limits. That constituted a “materially adverse change of contract” per Sprint’s terms; this opened a porthole for unhappy Sprint customers to jump ship without incurring early-termination fees, which can amount to $150 or more. Similar changes in administration fees allowed T-Mobile users to switch last September and Verizon users to opt out in the spring of 2008.
The Fix: If your provider changes terms, and you decide to leave as a result, contact the company within the time period specified in your contract (usually 30 to 60 days). Make it clear that you’re switching because of the “materially adverse” nature of the change.
[Update] They don’t live for work … they work to live | they don t know about us แปล – NATAVIGUIDES
Settling down on the shiny black sofa in the front room of their student house in Jesmond, Newcastle, Ailsa McNeil and her flatmates discuss what they would do once they had left university.
‘The idea of moving into the financial world of London and working long hours inside a massive company does not appeal to me,’ said McNeil, placing a textbook down on the cream carpet, among scattered magazines, scarves and revision notes. The 20-year-old had a final-year exam for her economics degree the next day.
People in their late teens and early twenties, she argued, were far keener to have a ‘good life with a standard amount of money’ than ‘slog’ their guts out like their parents. ‘I saw my mum and dad work really hard, but my work ethic is different,’ said McNeil. ‘I want to do well but I want to have great fun in life. Money and work are not the be all and end all. If you put all your effort into your job you lose sense of what you are living for.’
McNeil is not alone. New research has found that a similar attitude to work is burgeoning among the group of people known as Generation Y – usually defined as those between the ages of 11 and 25. A study of more than 2,500 people born after the early Eighties found that they were rebelling against their parents’ values and were determined not to lead lives that revolved so heavily around the world of work.
Instead, they were ready to resign if their jobs were not fulfilling and fun, with decent holidays and the opportunity to take long stretches off for charity work or travel. Salary and status were not high on the priority list, according to the study by Talentsmoothie, a firm that consults companies in banking, professional services and the law on the changing workforce.
Here is a group that has never known, or even witnessed, hardship, recession or mass unemployment and does not fear redundancy or repossession, according to researchers. The result is a generation that believes it can have it all and is not embarrassed to ask for it; a generation that will constitute the majority of the workforce within a decade.
That is why major companies, embroiled in the battle to attract the very best graduates, are doing whatever they can to lure them in. ‘The previous generation saw work as a primary part of life,’ said Madalyn Brooks, HR director at Procter and Gamble. ‘When they left education, work was a dominant part of what they did and they were not looking for time out. Now we are seeing the growth of a different profile of candidate. They have grown up in relatively affluent families. They want to be sure that they can strike a balance between work and their personal life, and so the opportunity to take time off, to travel, to work for a company with a strong social responsibility record, these are all concerns that we increasingly hear when recruiting talent.’
Procter and Gamble has already adapted its recruitment efforts and what it offers to meet the needs of Generation Y. Instead of just stressing higher salaries, this international company is highlighting the opportunity for flexible hours, the chance to work from home, the offer of up to a year of ‘family leave’ to look after children or elderly parents, and the promise of regular three-month sabbaticals. Similar packages are being offered by companies across Britain.
In his open-plan office in the centre of Aberdeen, Simon Chinn, 25, a senior consultant at a recruitment agency, rushed between meetings last week. He admitted that one thing that attracted him to the firm, Thorpe Molloy Recruitment, was the fact that it was flexible when employees asked for time off. In two cases colleagues travelled for a year before returning to the same job.
Chinn argued that it also played an important role for the candidates he was helping to recruit. ‘There is an oil service company in Aberdeen that has a very attractive benefits package,’ he gave as an example. ‘There is a good pension, gym membership in the office, opportunities for travel and sabbaticals. People can take time out and come back to the job. That does attract the best talent.’
The fact that young people changed jobs more frequently, argued Chinn, meant they were less willing to put up with long hours or poor holidays. Officials in the US have estimated that a typical member of Generation Y will have 10 jobs by the age of 38. ‘People think, why stay in a job you do not enjoy?’ he said.
In Newcastle, McNeil and her flatmates reached a similar conclusion. ‘If a company offers more flexibility, it is a sign that it has the type of culture you would want to join,’ said the undergraduate, who has signed up to the Milkround, a graduate recruitment network.
The fact that she now receives more than 20 emails a day from employers makes her feel more confident about her future options: ‘It is as if people expect to get a job. I also think that, unlike our parents, we feel like we have financial back-up if things go wrong. But I guess that could change if we enter a recession.’
It is the lack of a significant downturn in the economy over the past decade and a half that is driving the new attitude, say experts. Generation Y: what they want from work, the research from Talentsmoothie, concluded: ‘They have only ever known economic prosperity. They have many choices: gap years and extensive travel are the norm. They can join a company, or set up their own. They have seen their parents in stressful jobs, working long hours, and realise that hard work for big companies apparently does not bring prosperity and happiness, or make the world a better place. They want their lives to be different – and this shows. If they are dissatisfied, they resign.’
The study found that 85 per cent of Generation Y wanted to spend 30 per cent to 70 per cent of their time working from home. More than half wanted a flexible working arrangement.
The top priority when choosing a job was ‘doing work that I love’. ‘Earning lots of money’ was far behind, in seventh place. When it came to walking away from an employer, a lack of motivation was the top reason followed by a work-life balance leaning too far towards the job. ‘The Boomer generation [who are over 45] created the culture of long working hours and Xers [aged between 28 and 45] reluctantly accepted it,’ the report said. ‘But not Generation Y. While they are not work-shy, they don’t live to work. They will get the job done on time … but on their own terms.’
The confidence, it said, came from a feeling of security: ‘Unlike Xers and Boomers, they are not remotely daunted by the spectre of unemployment.’
Simon Walker, a founding director of Talentsmoothie, said this generation considered work something to do, not somewhere to go. ‘As long as they achieve what they need to they are not worried about being seen to do it at their desks,’ he said, explaining why things were different for the older generation. ‘I am 40 and when I was 10, 12, 14, there was the winter of discontent, Thatcherism and miner strikes. Three million were unemployed, so subconsciously employment was seen as precious and there was no such thing as a secure job. For the next generation, there was full employment, unprecedented economic growth. Their attitude is: “If I can’t get one job, I will get another one.” They are not preconditioned, like many of us, to be cautious of authority.’
In fact, the research found that younger workers were far more willing to challenge managers and were undeterred by traditional hierarchy. Walker said he was trying to help ‘Boomer’ and ‘Xer’ managers to understand the new attitude and not get frustrated by it. Much of what the workers were demanding, he said, such as work-life balance, personal development, exciting jobs and motivating managers, would be welcomed by older workers as well. But the clash of values was causing friction in offices.
In one case, outlined in the study, a chief executive of a large insurance firm emailed thousands of employees to inform them about a major decision. Sitting at his desk in the middle of the huge office, James, 24, who had recently joined the firm, told his older colleagues he disagreed with what had been done. He quickly decided to share his feelings with the head of the company and sent his thoughts directly to him in an email.
Within minutes, a reply popped up on James’s screen: ‘I have been running this company for 10 years; I think I know what I am doing.’ Still undeterred, he hit back: ‘I realise this is an uncomfortable conversation but I am not the only one that disagrees with you.’ Luckily he was able to convince the boss that he was not simply being rude.
The overconfidence of Generation Y is proving a challenge for employers. This summer the Association of Graduate Recruiters will host a conference, at which delegates will debate how far firms need to go towards accommodating the desires of younger workers and how seriously they should take the concept of Generation Y.
Carl Gilleard, chief executive of the AGR, recently described young workers as ‘opinionated’ and more demanding of employers. He said: ‘One colleague who recently faced a barrage of questions about what her firm will give one young man, was forced into reacting with the question, “And what are you going to give us?” ‘
While warning that those who did not make an effort to respond to the needs of this group would end up ‘dead in the water’, Gilleard added: ‘Just how far do employers lean over backwards before they end up being horizontal?’ Others felt that companies should not ‘overreact’ to the new values and attitudes, warning that things could soon change again.
Helen Bostock, global head of campus recruiting for the investment bank Credit Suisse and a board member of the AGR, said: ‘A few years ago I recall the dotcom bubble when everyone was trying to reinvent themselves with an entrepreneurial culture. Now it is generational theory. What happens is that employers get sucked into the whole thing, then the pendulum swings one way or another. One thing that is consistent is that there is always something we are tackling. If it is not work-life balance, it is diversity, inclusion or something else.
‘In reality large graduate recruiters take much longer to change and there is a danger that employers will overreact and reinvent themselves as something they are not.’ Bostock gave the example of the ‘dress-down’ craze, when thousands of firms encouraged their employees to come to work in more casual attire each Friday. ‘That does not happen now, people have largely returned to the world of suits,’ she said.
Given her global role, Bostock argued that Generation Y differed from country to country and warned that the time for UK graduates to be complacent about job opportunities would soon come to an end.
‘There are highly talented individuals from China and India heading our way,’ she said. ‘They are hungry, focused on work and focused on academic success. Just look at the number of high-achieving Asian women studying maths and science compared with home-grown students. This generation is facing different challenges.’
Walker said he planned to look at how attitudes differed across the world. He argued that ‘generational attitudes’ were partly dictated by age but also circumstances. In China, Generation Y was made up of only-children, as a result of the one-child policy, who grew up through difficult economic times. They would have very different values to their British counterparts, he said.
In Britain, meanwhile, there would be people of all ages who shared typical Generation Y attitudes, he argued, but they would be far more common within the age group. One of those attitudes, according to research by Walker and others, is an overwhelming desire to be fulfilled in their jobs.
A study in 2004 carried out by Common Purpose, an organisation that offers training for leaders and managers, found that those who were not getting satisfaction at work were hitting a ‘quarter-life crisis’. Searching for Something concluded that employers had to accommodate young workers’ wider ambitions or risk losing them by the age of 30.
‘We see young people that are searching for some sort of meaning in life and if you can’t align their values with the organisation they might leave,’ said Julia Middleton, the group’s chief executive. ‘I think life is cyclical – and there is a return to people searching for meaning and searching for values.’
Middleton agreed that economic prosperity had fuelled the values of Generation Y. ‘If you haven’t had money or faced the serious threat of not having money, you take money much more seriously,’ she argued. ‘We have a generation that has not felt the threat for some time.’
Now, for the first time in many years that threat is returning. While it may come as an uncomfortable shock for those self-assured members of Generation Y, it could also create a whole new work ethic among the toddlers and babies that constitute Generation Z; born after 2002 they still have a long way to go before they are thrown into a whole new world of work.
I don’t want my parents’ life
Aditi Horsburgh, 25, works as a PA in London
My dad works in the hotel industry, and that is a 24-hour job. He has always worked really hard. A lot of the time he could not take holidays or spend time with us. I appreciate what he did, but I don’t want that to be my life. I don’t want work to be so full-on that you cannot enjoy your family. I think my father’s attitude came from the fact that he did not have much when he was growing up. I am in a different situation. My parents worked very hard to give me what I wanted, and I am really grateful for that. I know that if I want to carry on with that lifestyle I will need to work, but I want to find a balance. I did a degree in business studies at Bristol University. Then I went to India to work for two years before doing an MA in media in London. I was looking for a job and I got in contact with Portfolio, a recruitment and headhunting firm for senior executive appointments in the leisure and hospitality industries. They offered me a job as PA to the chief executive and I hope they will train me up to become a consultant.
Obviously I want something to pay the bills, but I am also interested in the work environment. I want to work close to home so I don’t have to commute too much. I value my free time and I love to travel. The company I work for is quite flexible with time off. I am taking three weeks in the summer to go glacier tracking in India. Others have gone on three-month sabbaticals.
From the Baby Boomers to Generation Z
As the war ended and the servicemen returned on a high, the Baby Boomers were conceived en masse. Born between 1946 and 1964, their early memories may include watching Bobby Moore lift the World Cup, the day Neil Armstrong stepped onto the Moon and the Vietnam War. As they grew up they donned mini and maxi skirts and bell-bottoms, listened to the Beatles and the Rolling Stones on vinyl, smoked cannabis, maybe dabbled with LSD, and took the new contraceptive pill. Next came Generation X, born between 1965 and 1982. Raised on television and early computers, they have been unkindly labelled by some the ‘me generation’ of the Eighties. They were the punks of the Seventies, listening to the Sex Pistols and the Buzzcocks. Lots were teenagers when cassettes made way for CDs. They wore leg warmers and ra ra skirts, shoulder pads and snoods. Most remember the Cold War, the miners’ strike, the birth of Thatcherism and the yuppie. Some smoked cannabis or took mushrooms while City high-fliers splashed out on cocaine.
The Baby Boomers’ children are Generation Y. Dubbed the ‘internet generation’, they owned computers and mobile phones, write blogs, listen to their iPods and download music. Born between 1982 and 2002, the older ones will remember the rise of boy-bands and Brit Pop. They loved Take That and the Spice Girls, Oasis and Blur. Some of them dabbled with ecstasy and witnessed the rise of the super-club. They watched shows such as Big Brother and Pop Idol as reality television took off. They roamed the streets in hoodies.
A lack of memory of life before the war on terror defines Generation Z. They are toddlers and babies, born after 2002. They probably spend their time learning baby yoga.
แปลเพลง They Don’t Know About Us – Victoria Duffield feat. Cody Simpson [แปลไทย]
ฝากกด Like 👍 กด Share 💁♀️ และ Subscribe ด้วยนะคะ 🔔
คอมเมนต์ติชมกันมาได้นะคะ ขอบคุณมากๆ นะคะ 🙏
แปลเพลง They Don’t Know About Us Victoria Duffield feat. Cody Simpson [แปลไทย]
➡️ Link Video: https://youtu.be/Mwwk2zV0Y8
📍 ติดตามอัปเดตข้อมูลข่าวสารของเราได้ที่ 👇
➡️ YouTube :
ขอขอบคุณ
Single : They Don’t Know About Us
Artist : Victoria Duffield feat Cody Simpson
μzikHubCodySimpson μzikHubCody μzikSimpson μzikHubTheyDon’tKnowAboutUs
μzikHub
เพลงสากลเพราะ ๆ ขอแต่งงาน ผู้หญิงร้อง
รวมเพลงสากลอกหัก เจ็บ ๆ เศร้าๆ
รวมเพลงสากลอกหัก เจ็บ ๆ เศร้าๆ
เพลงฟังแล้วร้องไห้
เพลงอกหัก ฟังกี่ครั้งก็เจ็บ
Thank you for watching
If there are some mistakes, please leave your comment.
This video is made for fun
Don’t mean to break the copyright regulation at all.
Thank you
วิดีโอนี้จัดทำขึ้นเพื่อความบันเทิงเท่านั้น มิได้มีเจตนาละเมิดลิขสิทธิ์หรือสิทธิส่วนบุคคลแต่อย่างใด
นอกจากการดูบทความนี้แล้ว คุณยังสามารถดูข้อมูลที่เป็นประโยชน์อื่นๆ อีกมากมายที่เราให้ไว้ที่นี่: ดูเพิ่มเติม
![แปลเพลง They Don’t Know About Us - Victoria Duffield feat. Cody Simpson [แปลไทย]](https://i.ytimg.com/vi/Mwwk2z-V0Y8/maxresdefault.jpg)
one direction – they don’t know about us (slowed + reverb) ✧
one direction they don’t know about us (slowed + reverb)
✧ i don’t own the song or the picture in this video, all credits go towards the original artist/owner ✧
enjoy!! ✧

They Don’t Know About Us – One Direction (Lyrics)
I don’t own anything. The rights belong to the owner.

แปลเพลง ไมเคิล แจ็คสัน #6 Black or White (ขาวหรือดำ)
No copyright infridgement intended
I am not intended to use the content for my own interest. This video is translated into Thai for Thai fans to enjoy and understand more about Michael Jackson.
ตามไปดู official music video นี้ได้ที่
https://www.youtube.com/watch?v=F2AitTPI5U0
ใครมีข้อเสนอแนะเกี่ยวกับคลิปที่อยากให้เราแปลก็คอมเม้นท์ทิ้งไว้ได้น้า
Thank you~ 🙂

Michael Jackson – They Don’t Care About Us (Prison Version) (Official Video)
“They Don’t Care About Us” by Michael Jackson
Listen to Michael Jackson: https://MichaelJackson.lnk.to/_listenYD
Spike Lee directed two short films for Michael Jackson’s “They Don’t Care About Us.” This version was filmed in a prison and was aired only at certain hours due to controversial content.
Subscribe to the official Michael Jackson YouTube Channel: https://MichaelJackson.lnk.to/subscribeYD
Watch more Michael Jackson videos: https://MichaelJackson.lnk.to/_listenYC/youtube
Follow Michael Jackson:
Facebook: https://MichaelJackson.lnk.to/_followYS/facebook
Twitter: https://MichaelJackson.lnk.to/_followYS/twitter
Instagram: https://MichaelJackson.lnk.to/_followYS/instagram
Website: https://MichaelJackson.lnk.to/_followYS/websitegeneral
Spotify: https://MichaelJackson.lnk.to/_followYS/spotify
Chorus:
Skin head, dead head
Everybody gone bad
Trepidation, speculation
Everybody allegation
In the suite, on the news
Everybody dog food
Black man, blackmail
Throw the brother in jail
All I wanna say is that
They don’t really care about us
All I wanna say is that
They don’t really care about us
MichaelJackson TheyDontCareAboutUs HIStory

นอกจากการดูบทความนี้แล้ว คุณยังสามารถดูข้อมูลที่เป็นประโยชน์อื่นๆ อีกมากมายที่เราให้ไว้ที่นี่: ดูบทความเพิ่มเติมในหมวดหมู่MAKE MONEY ONLINE
ขอบคุณมากสำหรับการดูหัวข้อโพสต์ they don t know about us แปล